The digital-first world demands every organization, whether big or small, to rely on technology. And that’s the path to innovation, progress and growth. However, along with it, comes the increased exposure to modern, sophisticated and cyber threats. Security leaders need to keep cyberattacks at bay. Moreover, the necessity of a strong security posture cannot be overstated to counter the growing threat actors. Vulnerability assessment stands as one of the initial, critical and sought-after essential elements of every organization’s security strategy.
Now to ensure your vulnerability assessment is effective, comprehensive and translates into success, you need to have some sort of a credible, complete checklist. A guide organization can follow to understand the process, key areas to examine, common pitfalls to avoid and how assessments tie into overall resilience.
What Is a Vulnerability Assessment?
Some define vulnerability assessment as a structured, though-out and systematic review of an organization’s IT assets. This mainly includes systems, applications and networks. However, this can extend to cloud, IoT and other technology adoptions. The aim is to identify weaknesses or, as experts casually say, holes that could be exploited by cyber attackers.
One question that can come up here is this: how does it differs from a security assessment? Well, unlike vulnerability assessment, security assessment takes a broader view of policies, processes and compliance requirements of your organization. Also, security assessments focus on governance and risk frameworks.
Why Businesses Need Regular Vulnerability Assessments
In simple words, because cyber attackers are growing in sophistication and creating new exploits every day to breach systems. Now suppose you run a retail business and possess an outdated point-of-sale (POS) system. “What could go wrong, you may think?” since everything seems to work fine. But without proper cybersecurity measures in place, missing patches and weak encryption could expose credit card data to potential theft. Therefore, discovering the issue after a breach could be catastrophic.
This story rings true, and history acknowledges it. It also mirrors what happens across industries and across the world. Invisible vulnerabilities constantly evolve, ready to devour weak systems. This is why regular, focused assessments will help organizations:
- To identify security risks in their IT system before attackers do get their hands on them.
- To assist security leader prioritize fixes based on severity and business impact.
- To achieve and maintain compliance easily and seamlessly with industry standards like PCI DSS, HIPAA or ISO 27001.
- To protect and retain customer trust by minimizing the likelihood of an incident.
The Ultimate Vulnerability Assessment Checklist
Now that you know about vulnerability assessment and how it can help your business, here is the checklist. It will guide you to turn this practice into something that will help boost security and business continuity.
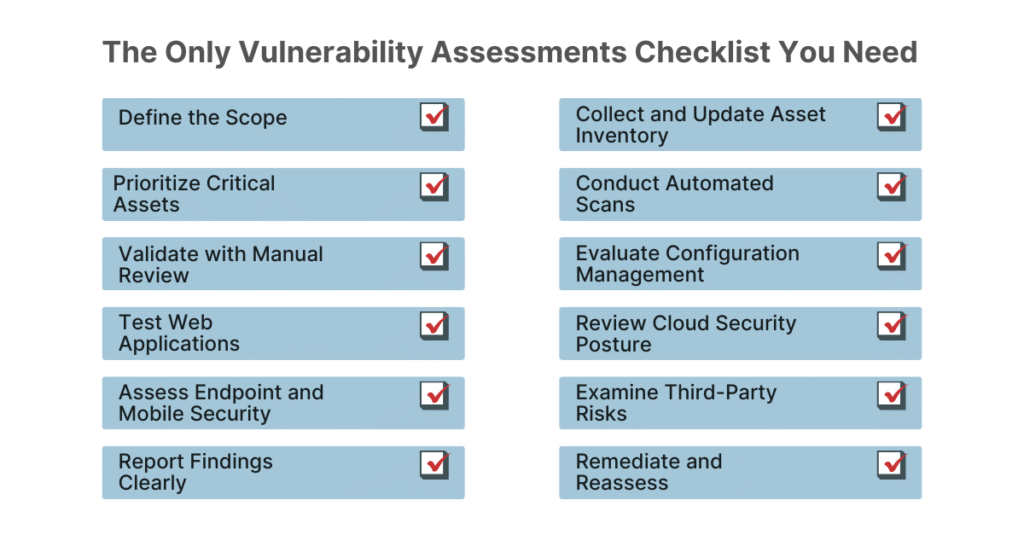
- Define the Scope
- Identify which assets, systems, and applications will be assessed.
- Include on-premises servers, cloud resources, mobile devices, and endpoints.
- Don’t forget third-party integrations—attackers often exploit vendor weaknesses.
- Collect and Update Asset Inventory
- Maintain an up-to-date list of all hardware and software.
- Note versions, configurations, and patch levels.
- Ensure shadow IT (unapproved apps or devices) is not excluded.
- Prioritize Critical Assets
- Identify systems that store sensitive data (e.g., customer information, financial records).
- Rank assets based on their role in business continuity.
- Focus resources on high-value and high-risk targets.
- Conduct Automated Scans
- Use vulnerability scanners to detect missing patches, misconfigurations, or outdated software.
- Regularly update scanning tools to cover the latest threats.
- Validate with Manual Review
- Automated scans often generate false positives.
- Security teams should manually verify critical findings.
- Context matters—what looks risky on paper may have limited real-world impact, and vice versa.
- Evaluate Configuration Management
- Review firewall, router, and server settings.
- Check for weak passwords, default credentials, or open ports.
- Ensure secure baselines are applied consistently.
- Test Web Applications
- Assess input validation, authentication mechanisms, and session handling.
- Watch for common flaws like SQL injection or cross-site scripting.
- Applications often serve as the “front door” to sensitive data.
- Review Cloud Security Posture
- Ensure cloud workloads follow the principle of least privilege.
- Check for misconfigured storage buckets or exposed APIs.
- Validate compliance with shared responsibility models.
- Assess Endpoint and Mobile Security
- Test for outdated antivirus or endpoint protection.
- Validate patching policies across employee laptops and mobile devices.
- Monitor bring-your-own-device (BYOD) risks.
- Examine Third-Party Risks
- Vendors and partners often connect directly into company networks.
- Ensure contracts include security requirements.
- Consider extending vulnerability scans to cover vendor-facing portals.
- Report Findings Clearly
- Categorize vulnerabilities by severity (critical, high, medium, low).
- Map findings to potential business impacts.
- Provide actionable recommendations for remediation.
- Remediate and Reassess
- Patch critical vulnerabilities immediately.
- Apply compensating controls where fixes are not possible.
- Reassess regularly to ensure improvements hold.
Commonly Observed Mistakes in Vulnerability Assessments
So, you decide to conduct a vulnerability assessment of specific IT assets which are critical and need protection. But you do not know the deeper level realities that could make it a failure. These are some of the pitfalls you should avoid making it a success:
- Treating assessment as a one-time task. Threats are evolving in breakneck speed, so assessments must be ongoing.
- Relying only on tools is another mistake. Automation is powerful but cannot replace human expertise.
- Ignoring low-level issues. Small flaws often combine and lead into larger exploits.
- Failing to act on results in hand. Identifying vulnerabilities without remediation offers little protection.
Vulnerability Assessment vs. Security Assessment
Understanding or revisiting the distinction between a vulnerability assessment and a security assessment is important. First, let’s see the definitions:
- Vulnerability Assessment: Technical focus, identifying and categorizing flaws in systems and applications.
- Security Assessment: Strategic view, assessing policies, procedures, compliance, and governance.
Both are essential. Also, foggy-eyed understanding could lead to poor decision making and cause damage to business.
How Vulnerability Assessment would look in Real World
Digital transformation is the buzzword today. Companies are adopting technology galore to make the process efficient. Image that you are a healthcare provider with cloud applications, IoT devices and sophisticated systems that store patient data. With digitization comes cybersecurity risks. To keep them at bay, a vulnerability assessment will unveil the following possibilities:
- Outdated medical devices running on unsupported operating systems, making them vulnerable to attacks.
- Weak authentication on remote access portals.
- Misconfigured cloud databases exposing sensitive data of countless patients.
A vulnerability assessment will remediate these issues. It would also mean reduced risk and easy compliance with HIPAA and other regulations.
Taking the Next Step
For organizations serious about protecting their operations, partnering with experts in Vulnerability Assessment can provide deeper insights and tailored guidance.
Cybersecurity is not just about tools—it’s about continuous vigilance, proactive detection, and effective remediation. Vulnerability assessments are the foundation of this approach.
Conclusion
We are living in a world where cyberattacks can come as a night storm and cause irreversible financial and reputational damage overnight. It is not a scary tactic but a reality, and organizations should not ignore this. A professional and experienced vulnerability assessment offers the visibility needed to identify weaknesses, prioritize remediation, and strengthen resilience.
By following a clear checklist and integrating assessments into broader security strategies, businesses can reduce risk and safeguard continuity. It’s not just about meeting compliance requirements—it’s about ensuring trust, stability, and growth.
For additional insights and resources on strengthening business resilience through cybersecurity, visit CyberNX.
